All Signals are Red: The Evolving Security Landscape
Solutions Customer Summit Series
If you are reading this, then you have Internet access. In this day and age, pretty much everyone from kids to employees not only have Internet access, but cannot make it through the day without that continual access. And while the advantages provided by the Internet can be vast, the risks that come with that access are also just as great.
Of course, corporations, Internet providers, and even the government are all doing their parts to attempt to limit the amount of risk that users might face while online. From regulations regarding privacy, to firewalls, anti-virus and intrusion prevention solutions, the amount of complicated technology that sits between your computer and the Internet continues to advance. And with all this amazing cybersecurity technology being implemented, you might think that your risks while online should be reducing. While an argument can be easily made that some types of attacks have been drastically reduced, the reality is that you are still going to face just as much risk today as you did a year ago or even a few years ago. In fact, many studies show that the amount of risk you face while online today is actually far greater than even just a year ago.

You see, while cybersecurity incident management software has become exceptionally better than in the past, the problem is that cyber criminals have also advanced in their forms of attacks. It’s the typical cat and mouse cycle that seems to never end: cyber criminals come up with a devastating new type of attack, then cybersecurity companies research the new form of attack and come up with a plan. A new product or service is introduced that directly mitigates the attack, and everyone breathes a sign of relief. Of course, a few weeks later the cyber criminals introduce another devastating new form of attack, and the cycle begins again. In addition, often times criminals may not even need to start from scratch; they simply evaluate the security tools that have been introduced to prevent their latest form of attack and then make minor changes to circumvent that new cybersecurity technology.
This of course should not deter an organization from implementing new cybersecurity technology, but employees need to be made far more aware about the limited impact that this technology can have in protecting them. Often times when new cybersecurity technology is implemented into an organization, employee computers become infected more instead of less often than before the technology was installed. At first you might assume that clearly the new technology is not as good as whatever was implemented before. In reality, the new technology was actually better. The real problem comes from the employees who are under the belief that the new technology is so good that they no longer need to worry about cybersecurity risks.
For example, when organizations implement strong anti-virus/anti-malware detection solutions on employees’ desktops, the assumption by the employee is that these solutions are preventing their computers from being infected. Therefore, when they browse on the Internet, click links in emails, or open attachments supposedly sent from co-workers, the employees’ concerns of becoming infected by malicious software is minimal since the assumption is that the security solutions implemented will obviously protect their computers.
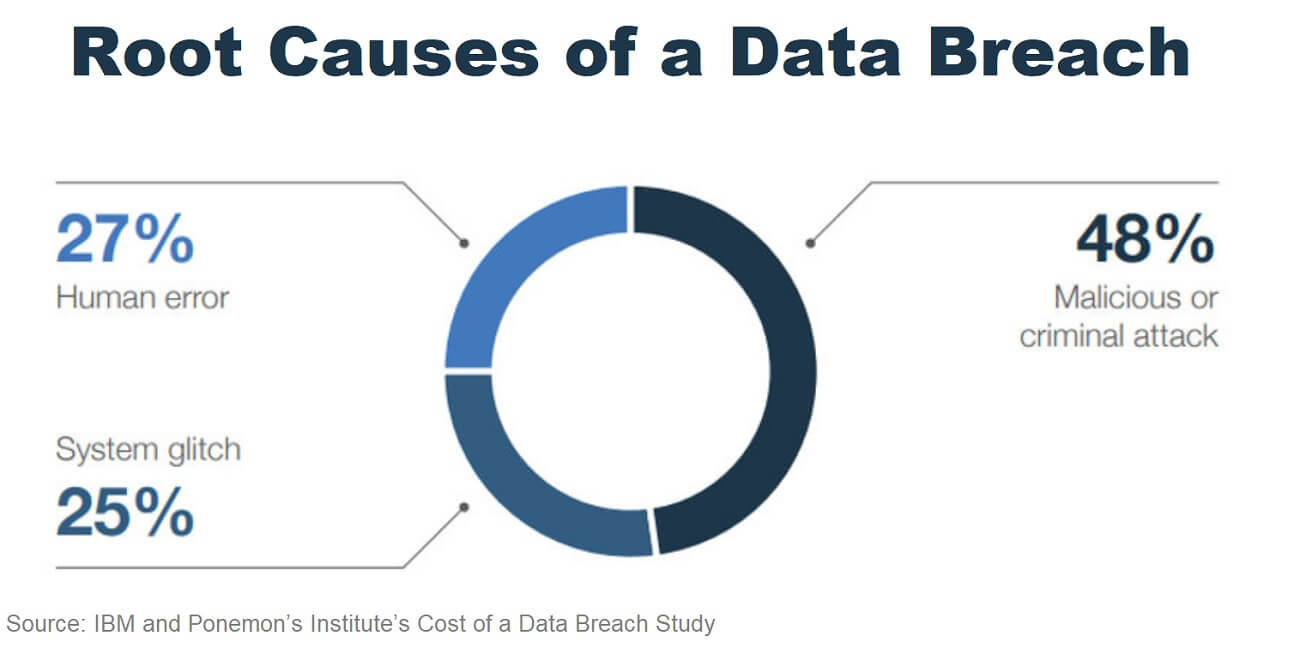
What many people don’t realize is that while it is good, security technology is not perfect. In fact, only 51% of new viruses introduced on the Internet are picked up by anti-virus solutions on day 1. After a new virus has been attacking the Internet for two weeks, that number increases to only 61%. That means that with each new virus working its way around the Internet, the technology on your computer designed to detect and prevent it only has a 61% chance of success.
Now, while that might seem like a decent chance of stopping the malware, on average new malware is released every 7 seconds. In just the first half of 2018, the amount of new malware was equal to all the malware that came out in 2017. And if you are thinking that maybe things got better as the year went on, well between December of 2018 and January of 2019, malware activity increased by 67%.
In addition, many organizations have implemented solutions that help protect web browsing by allowing organizations to choose the types of content that are safe for users to access. The problem is that even websites deemed safe have been found to spread malware. According to cybersecurity company Sophos, 82% of malicious websites are actually hacked legitimate websites. This means that even with strict security policies in place that limit users to only the most well-known and legitimate websites, a user could have still been infected by simply visiting a legitimate site that had been compromised. But again, if the users browsing on the Internet are under the impression that they are secure because the organization is keeping their web access secure, they are less likely to worry about the sites visited.
The same holds true with email when organizations provide filtering and security notifications. For example, many organizations implement rigorous filtering on their inbound email to reduce the risk to users from receiving potentially malicious email. Often emails will contain a header message indicating if the email was sent from an employee internally or if it was received from someone on the Internet. By implementing these additional layers of security, the recipient can feel more confident about emails received because they have gone through security screening. Again, the problem is that while filters and email sender notifications help, they offer no real guarantees and often give the recipient a false sense of trust. For example, if you receive an email that comes from a co-worker, it is much easier to trust it. If that email has also been flagged to confirm it truly was sent internally, it adds even more credibility that it is legitimate. So, if that email includes a link or attachment, you’re more likely to click the included link or open the attachment because it was from a trusted co-worker and flagged to show that it really was sent from an internal user. Had the email not contained the flag showing it was truly sent from an internal user or had it not been sent from a co-worker, you may have been more suspicious.
The problem is that criminals are using this level of trust against organizations. They are sending emails that appear to be from co-workers and in some cases, using already compromised computers in an organization to send more emails to other employees. Those emails are now flagged as sent from internal users allowing the cyber criminals to compromise even more systems on the organization’s network.
So, what does all this mean? Obviously cybersecurity solutions are extremely important to the security of any company. However, you should understand that they are not the total solution. At best, they can slow intruders down and make it more difficult for would-be attackers to gain access. That said, ultimately, even the best security in the world is not a guarantee. In fact, regardless of how good you might think the security is implemented at your organization, you are still at risk. Every time you connect to the Internet via your computer, tablet, or mobile device, potential threats will present themselves, and it is up to you to keep your guard up. Never assume that the information risk management system will protect you. Sure, it may be implemented, but it is nothing more than a backstop that hopefully might catch something you missed. The reality is that you are on the front line of defense, and it’s far better for you to avoid and/or detect a malicious situation than to hope that automated software will do it for you.



