Do you have a data breach response plan?
IT Governance BC
JANUARY 7, 2019
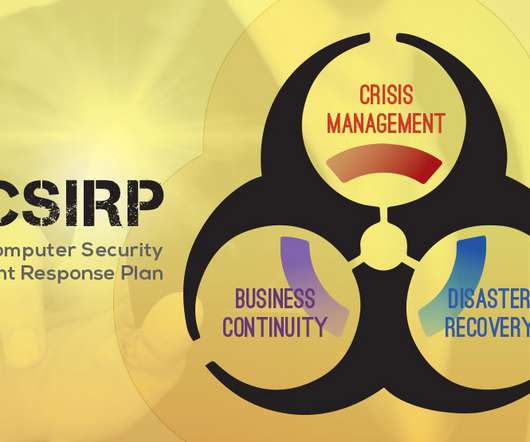
This blog has been updated to reflect industry updates. Originally published 6 August 2018. The EU GDPR (General Data Protection Regulation) requires organisations to respond to serious data breaches within 72 hours of detection. This places a significant burden on organisations: taking the appropriate measures to comply with the law while simultaneously dealing with the collateral impact of a breach is not a picnic!





















Let's personalize your content