
Up and to the right.” We’ve probably all heard this expression before, usually to describe an event that is moving in the right direction — such as company’s growth, or a stock’s performance over time. Unfortunately, however, it also describes the number of cyberthreats and attacks over the last decade (or longer). Worse, such a trendline has predicted spikes through 2020 and beyond as cybercriminals have taken advantage of unprecedented vulnerabilities caused by the COVID-19 pandemic.
Clearly, the threat of cyberattacks will continue in the future, both in number and potential severity. In fact, many experts fear that a major event — the “big one” — is still looming, with the very real probability of causing much more disruption than we’ve seen so far.
All of this points to an even greater need for cyber protection and cyber resilience. While these terms are often misunderstood or considered interchangeable, they actually represent two different cybersecurity concepts. It’s more critical than ever that companies include both cyber protection and cyber resilience as part of their overall defense strategy. In an effort to help, this article will describe these two concepts; explain how and why they’re different; and show how Acronis solutions can help with both.
What are cyber protection and cyber resilience, and how are they different?
We recently published an article (LINK) that described the differences between cybersecurity and cyber resilience. Here is a brief refresher on those two concepts as well as an overview of cyber protection.
· Cybersecurity refers to a company’s ability to protect against cyber threats and cyberattacks. It generally describes the various technologies, processes, and practices to safeguard a company’s vital assets, including networks, data, systems and applications, and infrastructure.
· Cyber resilience describes the quality of IT infrastructure that is pliable and robust enough to withstand changes and modifications, and can rapidly return to a stable state. These changes and modifications can include a cyberattack, the onboarding of new employees, adding new endpoints or workloads to the network, hardware failures, or a merger or acquisition — in short, any activity that changes and “disturbs” the status quo.
· Cyber protection is the integration of cybersecurity and data protection. While cybersecurity protects against cyberattacks, data protection ensures that your clients’ data is safe and recoverable because it is backed up and available in the event of data loss caused by any event. Experts recommend that cyber protection provides the maximum defense against cyberthreats and cyberattacks.
How does cyber protection contribute to cyber resilience?
Cyber protection ensures that your data is safe, regardless of any event. For example, if your client suffers an attack and loses their data, they can only recover the data if they use a cyber protection service that provides system backups. Backups, in turn, make an organization cyber resilient. Backups are an example of how an organization can return its infrastructure to a stable state when an attack happens.
To meet the objectives related to cyber protection, companies need technological solutions that address the five vectors of cyber protection. Collectively known as “SAPAS,” these include safety, accessibility, privacy, authenticity, and security.
· Safety — Ensuring that a reliable copy of data is always available.
· Accessibility — Making data available from any physical location, at any time.
· Privacy — Providing full control and transparency over who can view and access data.
· Authenticity — Ensuring that backed-up data is an exact, unmodified replica of the original data
· Security — Protecting data, apps, and systems against cyberthreats and cyberattacks.
Do my clients need both cyber protection and cyber resilience?
Yes! Your clients need both cyber protection and the ability to be cyber resilient. Companies need to use all the tools and approaches at their disposal to protect themselves. This means that companies should incorporate cyber protection and cyber resilience into their overall cybersecurity program.
Acronis Cyber Protect Cloud: Full stack cyber protection for your clients
Acronis can address all these concerns with integrated solutions that enable comprehensive cyber protection — because they’re built to address the five vectors of cyber protection at every step, from the underlying infrastructure to the cloud-based delivery platform.
Acronis Cyber Protect Cloud is a platform that enables service providers to deliver cyber protection in an easy, efficient, and secure way. With one solution, users gain access to backup, cloud disaster recovery and DraaS (disaster recovery as a service), ransomware protection, file sync and share, and blockchain-based file notarization and e-signature services — all managed from a single console.
The Cyber Protect Cloud also helps managed service providers (MSPs) expand their services with advanced protection packs, which include the following:
Advanced Security. Take advantage of integrated cyber protection that includes full-stack malware prevention. This solution extends the endpoint capabilities of the Acronis Cyber Protect Cloud, helping MSPs reduce the risk to clients with enhanced anti-malware protection and remediation services.
Advanced Backup. This integrated approach to cyber protection enables service providers to extend the cloud backup capabilities clients require to proactively manage their data.
Advanced Disaster Recovery. Now MSPs can get their clients back to business in just minutes and ensure immediate data availability after a disaster strikes. The Advanced Disaster Recovery add-on helps make disaster recovery painless and increases efficiency with orchestration, runbooks and automatic failover.
Only integrated cyber protection solutions can provide effective security for entire modern workloads across multiple domains — and keep up with the risks presented by constantly evolving, cutting-edge cyberthreats.
Acronis integrates backup, recovery, and next-generation machine intelligence (MI)-based anti-malware and protection management into one solution. This integration and automation provide complete cyber protection while increasing productivity and decreasing TCO.
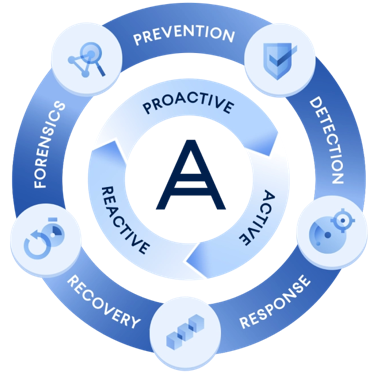
With one agent, one web-based management console, and one license, you can remove the complexity and risks associated with non-integrated solutions while ensuring your clients benefit from the five critical stages of cyber protection — prevention, detection, response, recovery, and forensics. This unified approach allows you to deliver easy, efficient, and secure cyber protection for your clients.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




