Top Architecture Blog Posts of 2023
AWS Disaster Recovery
FEBRUARY 28, 2024
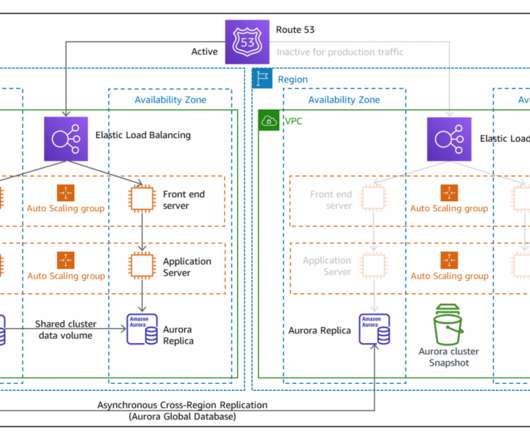
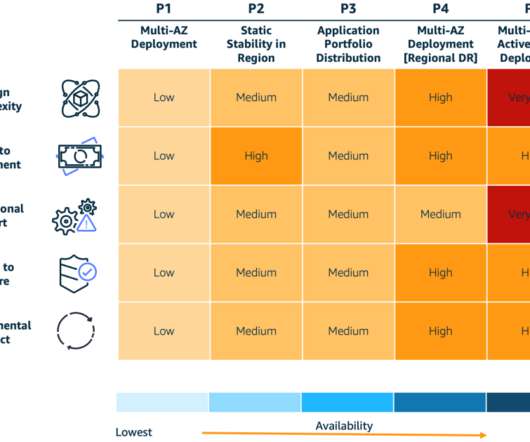
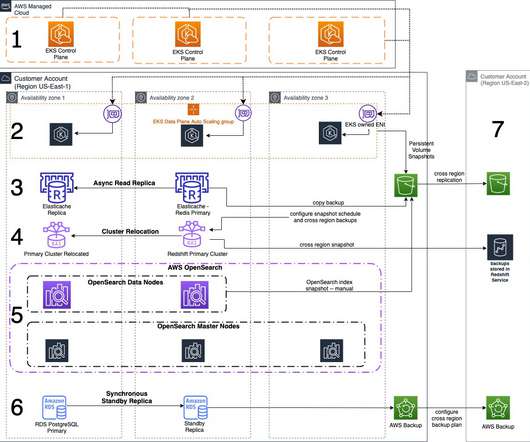
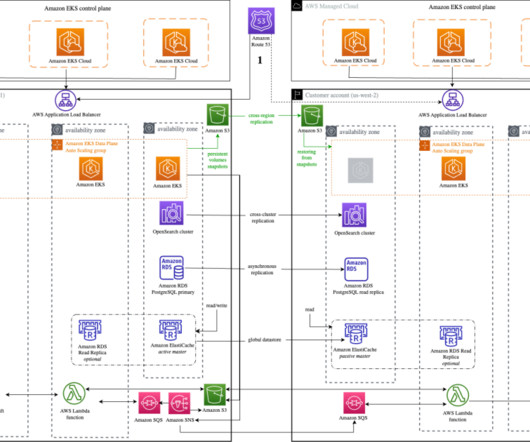
2023 was a rollercoaster year in tech, and we at the AWS Architecture Blog feel so fortunate to have shared in the excitement. Building endless aisle architecture for order processing Check it out! #9: Warm standby with managed services Check it out! Reusable ETL framework architecture Check it out! #4: Figure 5. #5:





































Let's personalize your content