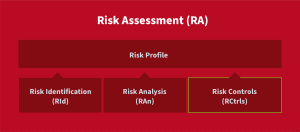
Risk Management Process – Part 3c: Risk Control
In our last post, we examined the risk analysis step of risk assessment. The third crucial step in risk assessment is risk control, which involves crafting effective strategies to mitigate the identified risks. There are four fundamental types of risk control: risk acceptance, risk mitigation, risk avoidance, and risk transfer.
The Importance of Risk Control
The significance of risk control cannot be overstated: it’s a critical element of the risk management process, enabling organizations to identify and manage the risks they face. Risk control’s critical importance lies in its ability to minimize the impact of potential risks and avert costly and disruptive events.
Effective risk control strategies enable organizations to take a proactive approach to risk management rather than merely reacting to threats as they arise. By developing robust risk control measures, organizations can avoid potential pitfalls, safeguard their operations, and protect their assets from harm. This proactive approach also helps to build resilience and maintain business continuity, even in the face of unexpected challenges.
Four Types of Risk Control
The four types of risk control— acceptance, mitigation, avoidance, and transfer—may seem distinct, but there is a gradient or continuum among them.
For instance, an organization may begin by accepting the risks associated with a particular project or activity. However, as the project progresses, the risks may become greater than anticipated, prompting the organization to implement mitigation strategies to reduce the likelihood or impact of the risk event.
Risk Acceptance
Risk acceptance is the type of risk control most suitable for risks with low likelihood and impact. In such cases, the organization can decide to accept the risk and its possible consequences without implementing any specific measures to mitigate or avoid it.
Risk acceptance is a feasible option when the costs of implementing risk control measures outweigh the potential impact of the risk event. It may also be a strategic choice when the organization has limited resources and must prioritize the most critical risks.
Even when an organization is not taking any action to address the risk, it’s still critical to monitor it closely and be prepared to react if the situation changes. This proactive approach will ensure that the organization remains alert and can act quickly if the likelihood or impact increases.
Risk Mitigation
Risk mitigation, the second type of risk control, involves developing and implementing strategies to reduce the probability of occurrence or minimize the impact of a risk. Risk mitigation can take one or a combination of the following approaches:
- Likelihood Reduction— This approach accepts the potential loss but attempts to reduce the probability of occurrence. For instance, an organization can reduce the vulnerability of a data center to high winds and floods by hardening the building and installing power backup generators. In cybersecurity, implementing security applications and conducting penetration testing would reduce the likelihood of successful cyberattacks.
- Loss Prevention— This approach accepts the potential risk but aims to prevent its impact. One example of loss prevention is cloud disaster recovery (DR), where an organization establishes a secondary DR site in the cloud to prevent the disruption of operations in case the primary data center is damaged or destroyed. The approach is achieved through duplication and diversification of resources, including on-premises and cloud infrastructure.
- Loss Reduction— This approach accepts both the potential risk and loss but aims to minimize the impact. Data backup is one such approach, where an organization accepts the potential data loss from a cyberattack but still minimizes the impact by managing data backups. While the organization still suffers some data loss (RPO), the loss is not total.
Risk Avoidance
The third type of risk control, risk avoidance, involves the complete elimination or avoidance of a risk. While this may not always be possible, it may be more effective in some cases to eliminate a risk entirely rather than managing it.
For example, an organization may choose to avoid a risk by relocating its data center to a geographic region that is less susceptible to natural disasters such as hurricanes. However, this approach may not always be feasible, particularly in situations where the risk cannot be entirely eliminated, such as cybersecurity threats that pose severe consequences.
Risk Transfer
Risk transfer involves transferring the risk to an outside entity that can manage and accept it. Organizations can choose to transfer risk to third-party service providers that specialize in managing specific risks.
For instance, an organization may opt to use public cloud infrastructure for their IT needs, which allows the cloud provider to manage all the risks associated with the infrastructure. However, the organization should be aware that the liability may still remain with them in case of a data breach or reputational damage in the event of a disruption.
It’s essential to thoroughly analyze and comprehend the risks involved before transferring them to third-party entities. Organizations should take care to assess the capabilities and reputation of the service provider and ensure that contractual obligations and responsibilities are clearly outlined. It’s also crucial to monitor the third-party provider’s performance continually, to ensure it is meeting its contractual obligations and that the risk is being adequately managed.
In our next installment, we are going to cover the final stage in risk assessment, the risk map, and go over a summary of that crucial step’s output.