Best practices for verifying and validating your backups
Acronis
MAY 10, 2023
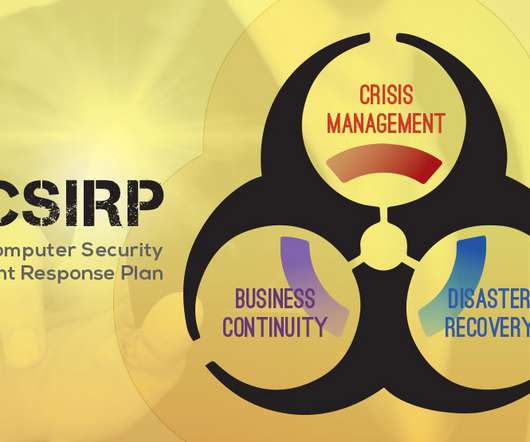
Many IT teams and companies think they’re successfully backing up their data and applications, only to have unpleasant surprises in the case of a malware attack, outage or other event. To overcome these challenges, you need to make sure you’re verifying that your backups are working exactly how you think they should.

































Let's personalize your content