Time to Fight Back Against Ransomware: Zerto Will Show You How
Zerto
MAY 24, 2022
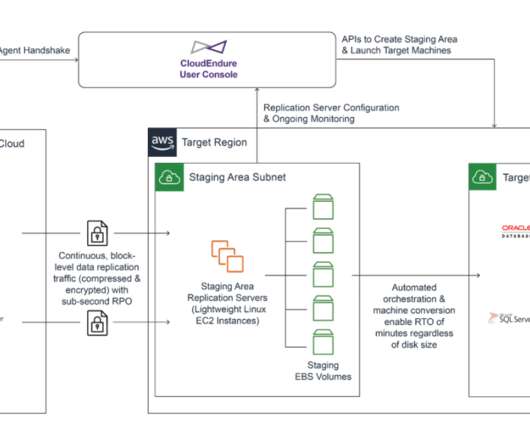
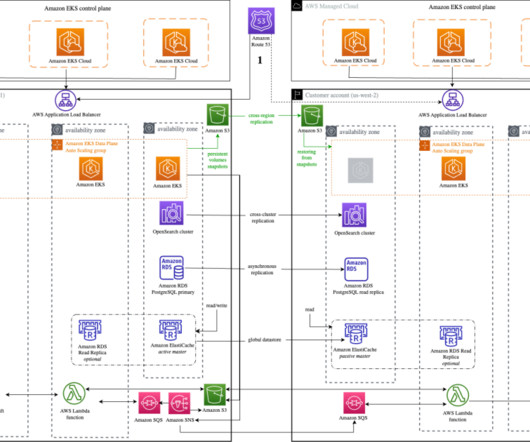
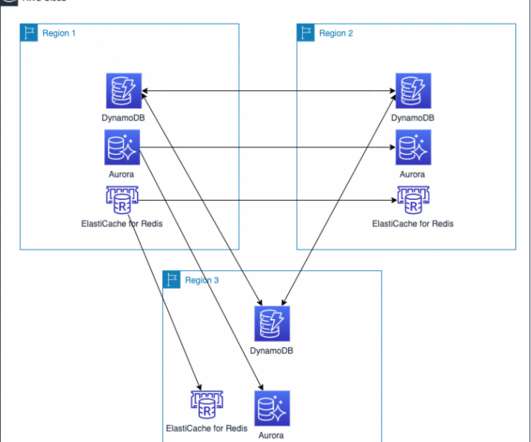
Through recovery operations such journal file-level restores (JFLR), move, failover test & live failover, Zerto can restore an application to a point in time prior to infection. This is where Zerto’s failover test and live failover functionalities help users recover from complete infrastructure meltdowns.














































Let's personalize your content