Cybersecurity in healthcare: How MSPs help safeguard patient data
Online Computers
MARCH 14, 2024
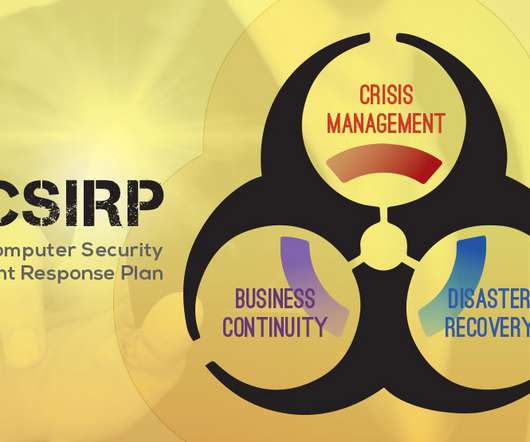
The importance of cybersecurity in healthcare A successful cyberattack on a healthcare organization has catastrophic consequences, including financial losses, operational disruptions, and compromised patient data. Malware – Malicious software can steal patient data, disrupt operations, or hold data hostage.

















































Let's personalize your content