Failover: What It Is and Its Importance in Business Continuity
Unitrends
MAY 15, 2023
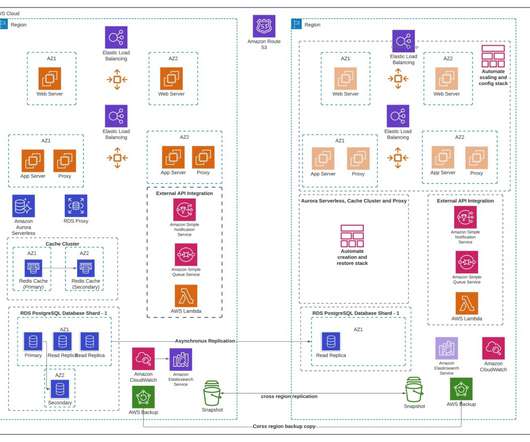
Have you ever thought about what a disaster might look like to your business without the ability to failover? Ransomware, hurricanes, floods, hardware failure, file corruption, human error and dozens of other disasters can bring business productivity to a standstill if your organization is not equipped to handle an outage situation.



































Let's personalize your content