Disaster Recovery (DR) Architecture on AWS, Part II: Backup and Restore with Rapid Recovery
AWS Disaster Recovery
APRIL 26, 2021
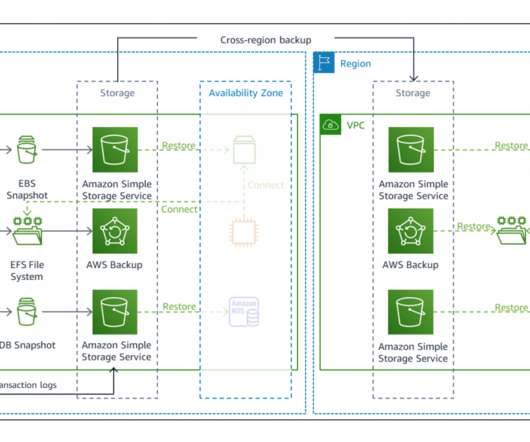
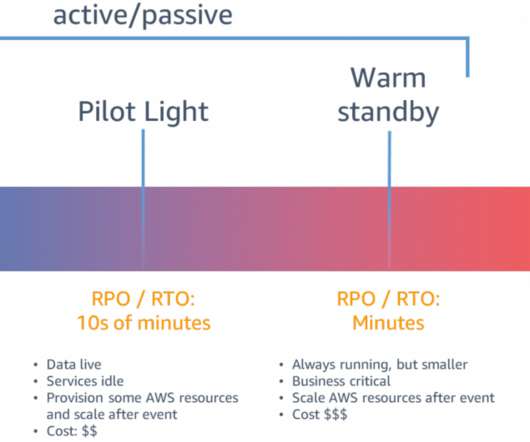
In a previous blog post , I introduced you to four strategies for disaster recovery (DR) on AWS. DR strategies: Choosing backup and restore. As shown in Figure 1, backup and restore is associated with higher RTO (recovery time objective) and RPO (recovery point objective). Implementing backup and restore.




















Let's personalize your content