Introducing Citrix Adaptive Authentication
Citrix
JUNE 1, 2022
This diversity has created a complex landscape of devices … The post Introducing Citrix Adaptive Authentication first appeared on Citrix Blogs.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Citrix
JUNE 1, 2022
This diversity has created a complex landscape of devices … The post Introducing Citrix Adaptive Authentication first appeared on Citrix Blogs.
Pure Storage
AUGUST 23, 2023
How To Use SSH Public Key Authentication by Pure Storage Blog Instead of using the same key to decrypt and encrypt connections, public key encryption uses a public and private key. What Is Public Key Authentication? Two keys are generated in public key authentication.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Citrix
MAY 23, 2022
Organizations may wonder whether application virtualization or desktop virtualization is the way to go. first appeared on Citrix Blogs. Desktop Virtualization: What’s the difference?

Citrix
MARCH 1, 2023
Last September, two important software industry players came together under the same roof: NetScaler , a leader in the load balancing and network security space that is used by 75 percent of internet users daily, and TIBCO , whose software … The post Why should you use NetScaler for TIBCO applications? first appeared on Citrix Blogs.

Pure Storage
FEBRUARY 14, 2024
New Pure1 Mobile App Features Enhance Security and Storage Optimization by Pure Storage Blog Introducing the latest evolution of the Pure1 ® Mobile Application! Receive push notifications for new requests, authenticate via external apps or SMS, and access request history. Figure 4: Biometric authentication.

AWS Disaster Recovery
DECEMBER 8, 2021
Building a multi-Region application requires lots of preparation and work. In this 3-part blog series, we’ll explore AWS services with features to assist you in building multi-Region applications. Finally, in Part 3, we’ll look at the application and management layers. Considerations before getting started.
Pure Storage
DECEMBER 7, 2023
by Pure Storage Blog When you have multiple operating systems and devices connected together, you need a centralized directory service to control authentication and authorization. Directory services also contain policies for printers, servers, applications, and other network resources that must connect to the environment.

Pure Storage
MAY 2, 2024
Every user and system, regardless of their location, must authenticate and validate their identity before accessing network resources. Every single new connection attempt should be treated with rigorous authentication and authorization. Identity verification: Multi-factor authentication is a fundamental aspect of zero trust.
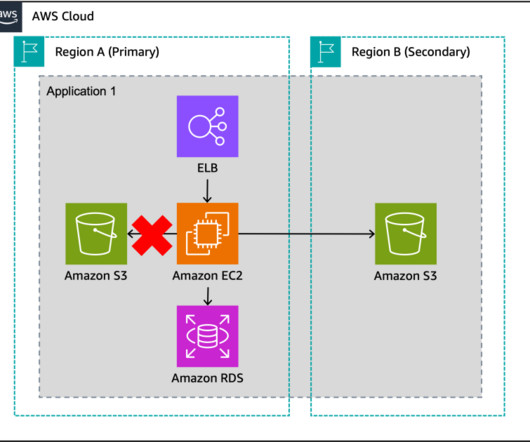
AWS Disaster Recovery
MAY 8, 2024
You can use these fault boundaries to build multi-Region applications that consist of independent, fault-isolated replicas in each Region that limit shared fate scenarios. However, applications typically don’t operate in isolation; consider both the components you will use and their dependencies as part of your failover strategy.

Citrix
FEBRUARY 27, 2023
In our mobile-first world, where hybrid work is the norm for many organizations, employees need access to corporate applications and resources from anywhere, on any device, on the go.

Pure Storage
JANUARY 5, 2024
Kerberos vs. NTLM by Pure Storage Blog Kerberos and NTLM, two prominent encryption methods, differ fundamentally in their approach to authentication and security. While Kerberos employs a robust third-party authentication system with ticket-based access, NTLM relies on a challenge-response mechanism and hashing techniques.

Citrix
OCTOBER 11, 2022
VPNs have long been a security standard for secure access to corporate applications. This blog post … The post Remote Access Without VPN: Is It Secure? first appeared on Citrix Blogs. Related Stories What is Authentication vs. Authorization?

Pure Storage
AUGUST 3, 2023
How to Implement Threat Modeling in Your DevSecOps Process by Pure Storage Blog This blog on threat modeling was co-authored by Dr. Ratinder Paul Singh Ahuja, CTO for Security and Networking, and Rajan Yadav , Director of Engineering, CNBU (Portworx), Pure Storage. What Are Authentication Bypass Attacks?

Citrix
JUNE 9, 2022
And leading companies around the world are using them to provide employees with access to the applications and insights … The post Citrix ZTNA solutions help organizations secure their remote workforces first appeared on Citrix Blogs.

Citrix
MAY 16, 2022
Citrix Application Delivery Management (ADM)???Citrix first appeared on Citrix Blogs. Citrix Features Explained: Increase app security with Citrix Secure Private Access Citrix Features Explained: Adaptive authentication and access in Citrix Secure Private Access. Citrix ADC?????????????????????????Pooled Pooled License????????Pooled

Citrix
FEBRUARY 27, 2023
In our mobile-first world, where hybrid work is the norm for many organizations, employees need access to corporate applications and resources from anywhere, on any device, on the go.

Citrix
OCTOBER 20, 2021
This is a guest blog post by Catherine Gallagher, Product Marketing Manager, IGEL Technology. Together, we deliver a … The post Empower your hybrid workforce with Citrix and IGEL Technology first appeared on Citrix Blogs.

Citrix
MAY 12, 2022
For your hybrid workers to do their best, most productive work, they need anywhere access to a wide variety of SaaS and web applications.

Pure Storage
MAY 7, 2024
The Power of Containers + AI: Why You Need a Data Platform That Supports Both by Pure Storage Blog Both AI and containerization have evolved rapidly into tech industry standards used by almost every major company across the globe. This elasticity ensures that applications can handle fluctuations in workload demand effectively.

Pure Storage
MAY 7, 2024
The Power of Containers + AI: Why You Need a Data Platform That Supports Both by Pure Storage Blog Both AI and containerization have evolved rapidly into tech industry standards used by almost every major company across the globe. This elasticity ensures that applications can handle fluctuations in workload demand effectively.

Citrix
MAY 23, 2022
This collaboration is powerful but can lead to confusion … The post Introducing System Log for the Citrix cloud platform first appeared on Citrix Blogs. Related Stories Application Virtualization vs. Desktop Virtualization: What’s the difference?

NexusTek
JANUARY 4, 2023
No technology blog would be complete without its annual “Tech Trends” article, so we’ve looked into our crystal ball to discover what we predict will be some of the most impactful trends in technology in the coming year. Specific Trend: Multifactor Authentication & Identity Access Management. READ TIME: 4 MIN. January 4, 2023.

Pure Storage
MAY 15, 2024
How to Deploy a Docker Image with Ansible by Pure Storage Blog Docker and Ansible are two powerful tools for automating software development and deployment. Docker is a popular containerization platform that allows developers to package applications into lightweight, portable containers.

Pure Storage
MAY 15, 2024
How to Deploy a Docker Image with Ansible by Pure Storage Blog Docker and Ansible are two powerful tools for automating software development and deployment. Docker is a popular containerization platform that allows developers to package applications into lightweight, portable containers.

Pure Storage
OCTOBER 23, 2023
Every user and system, regardless of their location, must authenticate and validate their identity before accessing network resources. Every single new connection attempt should be treated with rigorous authentication and authorization. Identity verification: Multi-factor authentication is a fundamental aspect of zero trust.

Pure Storage
MARCH 29, 2024
World Backup Day: Four Data Protection Best Practices to Know by Pure Storage Blog This article originally appeared on SolutionsReview.com. The post World Backup Day: Four Data Protection Best Practices to Know appeared first on Pure Storage Blog. It has been republished with permission from the author.

Pure Storage
DECEMBER 27, 2022
Another box provided user authentication, and so on down the line. This offered tremendous savings and simplification (read more in our blog post on NFV ). Learn more in our blog post on the CNF revolution. They grew their effective storage capacity by 188%, which was needed for new applications. One box answered calls.

Pure Storage
FEBRUARY 12, 2024
Harnessing Static and Dynamic Code Scanning in DevSecOps by Pure Storage Blog This blog on static and dynamic code scanning in DevSecOps was co-authored by Dr. Ratinder Paul Singh Ahuja, CTO for Security and Networking, and Rajan Yadav , Director of Engineering, CNBU (Portworx), Pure Storage.
Pure Storage
JULY 12, 2023
Brings Next-gen Performance for on Premises and Hybrid Cloud by Pure Storage Blog We’re excited to announce that Purity//FA 6.4.7 You can find out more by visiting the technical announcement blog post. This means that Pure Cloud Block Store can now be used to host business-critical applications such as databases. Purity//FA 6.4.7

Pure Storage
JANUARY 22, 2024
Blob Storage vs. File Storage by Pure Storage Blog Azure Blob Storage and Azure File Storage (officially called Azure Files ) are both Azure services designed for storing data in the cloud, but they serve different purposes. This enables easy integration with existing applications and systems.
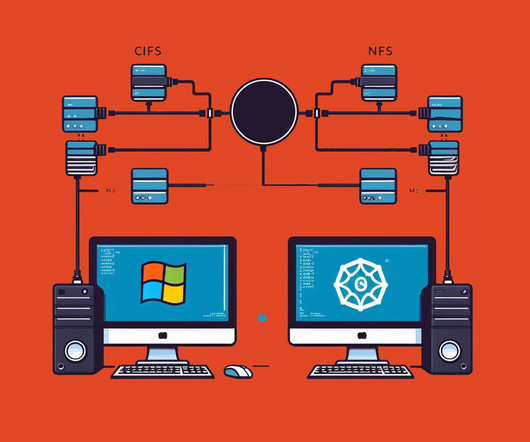
Pure Storage
NOVEMBER 29, 2023
by Pure Storage Blog In today’s enterprise IT landscape, seamless data sharing is imperative for efficient operations. Features: NFS offers strong support for large file systems and concurrent access, making it ideal for data-intensive applications. CIFS, on the other hand, excels in user authentication and access control.

Pure Storage
DECEMBER 18, 2023
7 Challenges with Applying AI to Data Security—and the Real Way to Solve Them by Pure Storage Blog As AI makes headlines and augments the way we work, there’s one area to be cautiously optimistic about: cybersecurity. However, its application is often labeled as proactive. Can it lend a hand?

Pure Storage
MARCH 6, 2024
Changes Continue in Cyber Insurance by Pure Storage Blog An ounce of prevention is worth a pound of cure certainly applies to physical health. Applications are commonly rejected if fundamental controls, such as multi-factor authentication, separate backups, and endpoint detection and response, are not in place.

Pure Storage
JULY 12, 2023
by Pure Storage Blog This article on CBS Terraform Provider 0.9.0 originally appeard on Adam Mazouz’s blog. In this blog post, I will cover what is new with the latest version of the Pure Cloud Block Store Terraform Provider. If you haven’t used it before, no worries, I’ve got you covered in this previous blog post.

Pure Storage
APRIL 14, 2022
This fine tunes secondary storage based on the importance of the applications or data needing protection. And to provide granular change management to prevent errors at scale, Auto-on SafeMode supports multi-party authentication. Security shouldn’t require one-size-fits-all compromise.

Pure Storage
FEBRUARY 2, 2024
Ransomware Attackers Find Fresh Targets in Cultural Institutions by Pure Storage Blog Ransomware attacks are big news when they hit giant corporations, government services, and resources like gas pipelines. Update and patch systems promptly.

Pure Storage
FEBRUARY 10, 2023
I will focus on authentication, the swagger option, and how to use it. A couple things about the Pure1 REST: Authentication is different than what is used with the FlashArray REST. A few that are one time only, and a few that are required for each authentication session: Create a PEM-based RSA SSL public/private key pair.

PagerDuty
OCTOBER 26, 2023
Teams might have any number of workflows that might benefit from a custom application. Creating custom applications for PagerDuty can help with those administrative tasks when another component is the System of Record for that data. We’ll use a sample application that our engineering team has published as an example.

Pure Storage
FEBRUARY 7, 2023
First, there’s the pre-op work, such as assessing the risks and checking on the health of the arrays, switches, hosts, and applications. The database and application teams needed to fail over their delicate applications to secondary instances. Many specialist teams had to get involved.

Pure Storage
SEPTEMBER 5, 2023
Why Encryption is Key to Cost Efficient GDPR Compliance by Pure Storage Blog The EU Digital Operational Resilience Act (DORA) reinforces the principles of the GDPR (adding to our GDPR compliance) to strengthen data protection measures for banking institutions operating within the EU.

Pure Storage
JANUARY 5, 2022
It works well for storing structured data and is often used for cloud-based applications. MySQL also supports enterprise applications, but some developers choose to port their application to MariaDB for performance reasons. The post How to Check Your MariaDB Version appeared first on Pure Storage Blog. Distrib 10.1.29-MariaDB,
OffsiteDataSync
JANUARY 7, 2022
Microsoft Office 365 is a critical SaaS application in remote and in-person workplaces. Microsoft ensures its service infrastructure is secure and that the application remains available. You can set up retention policies for storage, recover granularly and secure access to backups with multi-factor authentication.

Zerto
DECEMBER 21, 2021
At the end of November, I blogged about the need for disaster recovery in the cloud and also attended AWS re:Invent in Las Vegas, Nevada. I covered this topic in more detail in my last blog post , but the highlights bear repeating in light of these recent outages. Outages are only one of many threats facing your data and applications.

Pure Storage
JULY 14, 2022
But having control when it’s spread across hundreds of different applications both internal and external and across various cloud platforms is a whole other matter. . In part 2 of our three-part cloud data security blog series, we discussed the issue of complexity. According to Cybersecurity Insiders’ 2022 Cloud Security Report : .
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content