Crisis Management Training: Practice Makes Perfect
Bernstein Crisis Management
FEBRUARY 19, 2024
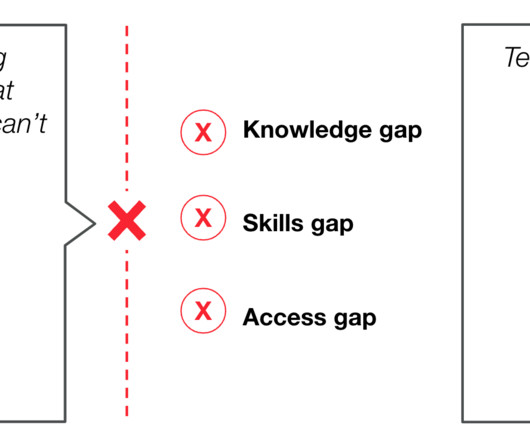
Spoiler alert: It’s not going to end well. Crisis management training equips individuals and teams with the skills and knowledge necessary to navigate and mitigate the impacts of crises efficiently. Decision-Making Under Pressure: The ability to make quick, informed decisions is crucial during a crisis.















































Let's personalize your content