Intelligent Alert Grouping: What It Is and How To Use It by Quintessence Anx
PagerDuty
OCTOBER 18, 2021
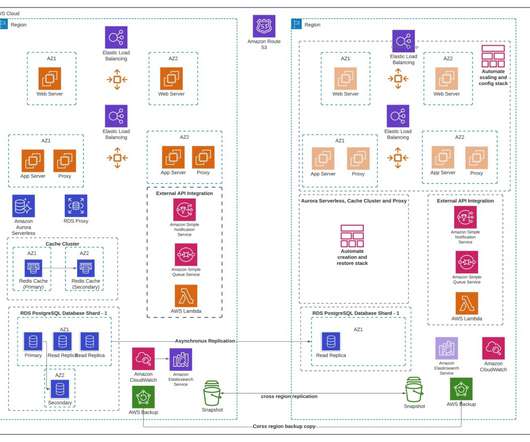
When the incident begins it might only be impacting a single service, but as time progresses, your brain boots, the coffee is poured, the docs are read, and all the while as the incident is escalating to other services and teams that you might not see the alerts for if they’re not in your scope of ownership.













Let's personalize your content