LDAP vs. Active Directory: What’s the Difference?
Pure Storage
DECEMBER 7, 2023
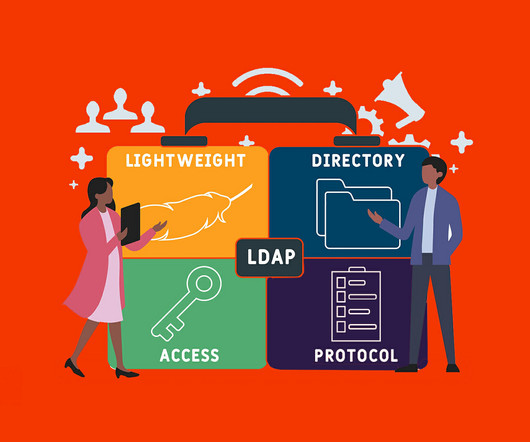
LDAP vs. Active Directory: What’s the Difference? by Pure Storage Blog When you have multiple operating systems and devices connected together, you need a centralized directory service to control authentication and authorization. As a protocol it can be used by various directory services including Active Directory. What Is LDAP?














































Let's personalize your content